Here is the summary of my livestream this morning. As surprising and shocking as this information may be, it is indeed true.
The only reason Wess Roley was in Coeur d’Alene, Idaho, was his role as a sexual lure in a US Government-run sting operation of law enforcement and fire leadership in the area. You can believe Wes Roley, a Broney Boy, held off three hundred State, Local, and Federal Agents in full battle rattle with dogs and drones for six hours with a shotgun, or you can believe there is more to the story.
We believe that Wess Roley could have been made aware of FBI Informant roles as a sexual lure through his stepfather, Tony Cuchiara, who was involved in the US State Department's Armed Diplomatic Security Services. Also, Billionaire Greg Carr’s Mossad-linked spy ring has known ties to Sheriff Bob Norris.
Part I – Setting the Stage
George Webb opens by warning viewers that the “bombshell” about Wes Roley will sound outlandish without first seeing the notorious videos of Roley in full makeup performing explicit stunts with a fish.
Those clips, Webb argues, prove Roley is not merely an eccentric twenty-year-old but a purpose-built sexual lure—a living honey-trap engineered to compromise the teenage CHILDREN of senior firefighter leadership and sheriff-level law enforcement in Kootenai County, Idaho.
In Webb’s telling, Roley’s function echoes the post-9/11 “Israeli art-student” networks that flooded U.S. police departments, fusion centers, and emergency services dispatch offices. Then, as now, he claims, a shadowy billionaire benefactor, Greg Carr, supplies patented wire-tapping kits—derived from Israeli telecom contractor Comverse and its spin-offs Verint and Amdocs—so that compromising calls, texts, and radio traffic can be recorded, cataloged, and ultimately weaponized for blackmail.
Greg Carr’s AmDocs recorded every call in the US before 9/11.
https://www.wanttoknow.info/9-11timeline60pg?utm_source=chatgpt.com
Webb alleges that Israel's spying on Greg Carr started by providing ComVerse backdoors into voice mail systems developed by Boston Technology, Carr’s company.
The pattern, Webb insists, is “textbook intelligence tradecraft”: insert an attractive or sexually transgressive decoy, capture the target’s indiscretions through covert intercepts, and hold the evidence until the moment the sheriff or fire chief resists a larger command-and-control agenda—at which point the kompromat becomes a leash. Coeur d’Alene, he says, is merely the latest small-town laboratory for a programme refined first in Los Angeles, New York, and Atlanta.
Part II – The Greg Carr / Comverse Apparatus
Webb frames billionaire tech philanthropist Greg Carr as the modern counterpart to Steve Feinberg: a venture capitalist whose fortune rests on data-exfiltration patents secretly shared with the NSA. Carr’s résumé, according to Webb, spans Boston Technology (voicemail “store-and-forward” systems), Comverse (call-duplication boxes), Verint (SS7 backbone exploits), and AmDocs wiretapping.
https://www.latimes.com/archives/la-xpm-1997-aug-22-fi-24751-story.html?utm_source=chatgpt.com
Carr also has a slew of synthetic-natural-gas (syngas) patents that give him entrée to Department of Energy and Homeland Security corridors.
After 9/11, Michael Chertoff allegedly blessed a deal whereby Carr’s gadgets—marketed as “Ultra” lawful-intercept tools—were delivered to regional intelligence centres (RICs).
Los Angeles’s RIC, where future Kootenai Sheriff Bob Norris once served, became the distribution hub. Carr’s scheme, Webb says, required more than hardware; it needed ultra-violet human assets who could slide into 3,000 county sheriff’s offices as dispatchers, admin staff, or “art students.”
https://www.salon.com/2002/05/07/students/?utm_source=chatgpt.com
Their job: install covert splitters on PBX trunks, courier voice packets to an Israeli server farm in the Negev desert, and supply local leadership with just enough counter-terrorism buzzwords to justify the intrusion. In big metro departments, the effort allegedly yielded kompromat that helped replace uncooperative sheriffs with pliant ones.
https://www.theguardian.com/education/2002/mar/06/internationaleducationnews.highereducation?utm_source=chatgpt.com
But to consolidate power nationwide, the same playbook now targets rural counties—hence Carr’s sudden philanthropy spree in Idaho and Montana.
Part III – Anatomy of a Sexual-Lure Operation
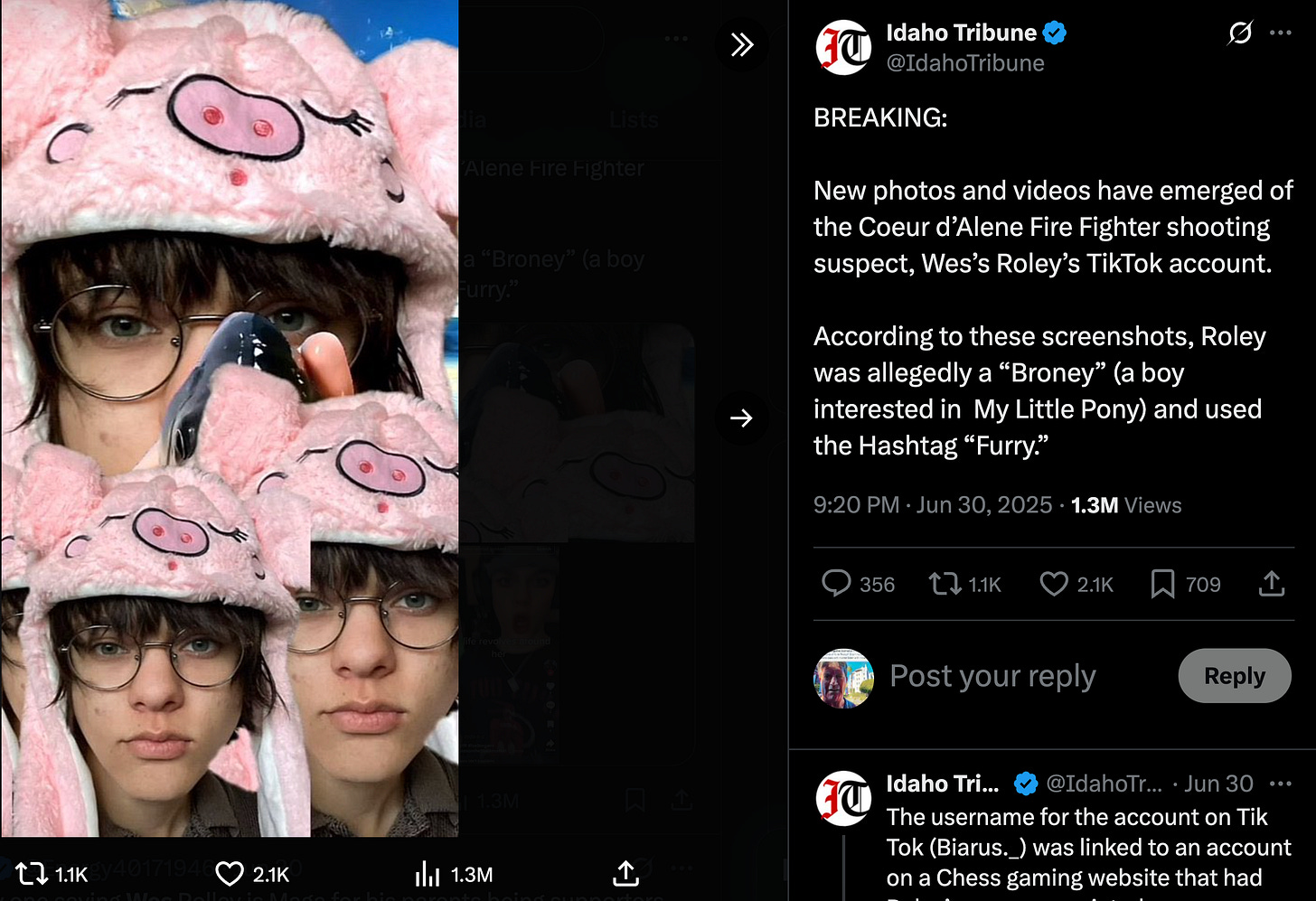
According to Webb, the Israeli art-student phase relied on conventionally attractive female decoys; the Kootenai iteration pivots to kink, cosplay, and blurred gender lines designed to ensnare both hetero and closeted targets. Roley—painted nails, white-van life, brony memes, “furry” avatars, fish-fellatio TikToks—embodies that shift. The same benefactor underwriting the Webb Roley operation is the same group associated with Greg Carr’s 9/11 “art student” organization.
Webb argues that any chief who invites such a persona into off-duty social circles is already six steps down the kompromat slide: private barbecues become photo ops; innocuous sexts become Exhibit A. Roley’s alleged handler, ex-special-forces sniper Travis Decker, supplies muscle and narrative misdirection: Decker can stage the lethal climax, plant the weapon, and leave Roley’s corpse to be discovered with incriminating paraphernalia.
https://www.congress.gov/committee-report/108th-congress/house-report/414/1
Meanwhile, Carr’s wire-tap boxes capture the chiefs in real-time crisis chatter—archived leverage for future demands. Webb underscores that the technique mirrors Steve Feinberg’s reported use of male prostitutes during BlackCube-run stings and is reminiscent of the 2012 West Webster fire ambush, where two volunteer firemen were killed after a lured vehicle blocked access. “If you wouldn’t believe a fish-blow video,” Webb quips, “you wouldn’t have believed Miloš Jovičić disguised as a dispatcher either—yet the sheriffs fell for her in 2003.”
https://www.intelligenceonline.com/political-intelligence/2002/02/28/israeli-spy-ring-uncovered-in-us%2C3294263-eve?utm_source=chatgpt.com
Part IV – Battalion 3 and the Fight over Unified Command
The strategic prize, Webb insists, is not salacious gossip per se but control over dispatch software. Kootenai’s independent firefighters favour “Battalion 3,” a drag-and-drop incident-command program co-written by veteran chiefs John Morrison and Les Holbrook.
Battalion 3’s virtue is precisely what federal integrators hate: it keeps fire, EMS, and police on separate channels unless mutual aid is explicitly requested. Carr-aligned firms prefer NE/RIS or Palantir-powered “unified incident” dashboards that merge every sensor, radio, and license-plate reader into a single pane—handy for SWAT teams arriving in MRAPs under a firefighting pretext.
Thus, Webb argues, the real victims on Canfield Mountain—Battalion Chiefs Morrison and Harwood—were system architects standing in the way of national rollout. The combined Fire and Sheriff architect is perfect to implement a “Use Fire As Human Shields” for a Federal takings operation.
By baiting Kootenai County Fire onto a narrow dirt road, Wess Roley reportedly delayed firefighters for forty minutes until the command staff arrived, and then Roley started murdering them with precision rifle shots, according to the Sheriff. And the psychological operations playing out on the mountain with firefight victims effectively decapitated local resistance in one afternoon.
Paving crews resurfaced the kill zone the next morning; the sheriff’s office refused to release CAD logs or body-cam footage; and suddenly, Palantir lobbyists were briefing the county commission on “next-generation resilience.” For Webb, the timeline reads less like coincidence than a hostile software acquisition executed at gunpoint. Of course, Webb immediately file records requests for all the radio traffic and body cameras of both police and fire services to get the proof of the official narrative.
Part V – The Psy-Op Narrative and Media Management
Webb dissects the official story: an unstable twenty-year-old with a shotgun, angry over firefighters pushing his white van, snaps and murders two chiefs before killing himself at 3:16 p.m. But radio recordings captured multiple rifle-calibre cracks and panicked calls of “active shooters—plural.” Yet by the 6:30 p.m. press conference Sheriff Norris hedged: “one, two, three, maybe four shooters,” then quickly emphasised the single-shooter narrative. The coroner’s preliminary findings? Delayed. The alleged murder weapon? Numberless. Roley’s digital footprint? Scrubbed within hours, even from TikTok’s Russian mirrors. Webb reminds viewers of 2013’s Aaron Alexis Navy Yard case, where the FBI sealed phone logs under “National Security.” Likewise, Kootenai deputies now cite an unspecified “federal hold” on releasing Roley’s phone or the battalion chiefs’ autopsies. At the same time, ABC runs B-roll of Roley’s childhood notebooks “covered in swastikas,” steering public outrage toward lone-wolf extremism—a profitable diversion for grant-seekers chasing DHS domestic-terror funds. In Webb’s framing, the media choreography is integral: it buries the multi-shooter evidence, erases the compromise-ops context, and primes taxpayers to accept militarised “all-hazards” fusion software as the salvation.
Part VI – Historical Precedents: From Crooks to West Webster
Webb connects Roley’s saga to earlier patterns: 2016’s Cecil “CJ” Crooks case in Pennsylvania, where another volunteer firefighter was blamed for sniper-level murders after his own death, and the 2012 West Webster ambush, which likewise involved a suspicious house fire, blocked apparatus, and precision shots. In both cases, Webb notes, dispatch archives vanished, commemorative legislation fast-tracked (the “Webster Provision” in New York; the “Crooks Act” in Pennsylvania), and commercial incident-command vendors exploited the outrage to market integrated solutions. Webb widens the lens further: Chertoff’s post-9/11 “Operation TIPS” had sought citizen informants to map critical infrastructure, but found sheriffs resistant. Enter Comverse and its art-student program. Twenty years on, the operation allegedly descends the municipal ladder: from NYPD to Spokane Valley to Coeur d’Alene. Each cycle upgrades technology (ISDN splitters, then LTE IMSI-catchers, now Starlink mesh antennas) while re-tooling the sexual lure (glamour girls, then female dispatchers, now gender-fluid TikTokers) yet the endgame—federal hegemony over county-level response—remains constant. Roley, in this genealogy, is the 2025 template: a meme-savvy lure seeded amid crypto-adjacent subcultures (bronies, furries, OnlyFans) to generate kompromat that older chiefs neither recognise nor can defend against.
Part VII – Syngas, Land Grabs, and the Economics of Fear
Why would a telecom wire-tap king invest in synthetic methane patents and north-Idaho land? Webb’s answer: layered profiteering. First, Carr’s syngas reactors promise “non-explosive” pipeline blends, marketable only after a wave of alleged methane explosions convinces NATO bases to ban Russian gas. Second, Kootenai County straddles unexploited shale plays; take command of fire and police, and you dictate evacuation zones, environmental permitting, even eminent-domain valuations. A conveniently timed wildfire or barn blast—responded to by unified fire/SWAT columns—lets operators roll MRAPs onto private ranches under a haze of “public-safety necessity.” Who complains when black-suited tactical medics accompany the hoses? Battalions that preferred independent software are already buried. And sheriffs who balk can be retired by leaked phone calls featuring, say, a brony-costumed Roley in compromising poses. “Cain will always kill Abel for the mineral rights,” Webb paraphrases. In this calculus, the Roley operation is the cheap down-payment on multi-billion-dollar resource arbitrage—gas molecules, data packets, and land titles bundled into a single extraction matrix. The pornographic kompromat is merely grease on the gears.
Part VIII – Evidence Suppression and FOIA Stonewalls
Webb recounts filing Freedom-of-Information requests for CAD logs, 911 tapes, body-cam footage, autopsy reports, and the van’s license plate—only to be told “three to ten business days” by county clerks before receiving silence. Paving crews obliterated ballistic evidence; Roley’s social-media history was vacuumed; and state troopers refuse to confirm whether rifle casings were collected separate from the purported shotgun. Even the Fish-Fellatio video—linchpin of the sexual-lure thesis—survives only as peer-to-peer shares. In Webb’s view, such speedy sanitisation implies prior coordination: cell-tower geo-fences might reveal an LPR hit by a blacked-out SUV leaving the scene; drone footage might show thermal signatures inconsistent with a lone gunman. Yet each data silo falls under a different pre-emption: federal fusion centers, FBI Evidence Response Teams, DHS Cybersecurity and Infrastructure Security Agency (CISA), or private contractors bound by NDA. The firewall is legal as well as technical; prosecutors slap “ongoing investigation” exemptions on everything. For Webb, the stonewall itself is probative: only an operation with federal sponsorship could orchestrate this breadth of suppression across multiple agencies in under 24 hours.
Part IX – Psychological Impact and the “Unified Response” Push
Beyond the tangible goals (software contracts, land control), Webb highlights the psy-op effect: firefighters—society’s untouchable good guys—slain in cold blood on the eve of Independence Day. The emotional shock primes voters to accept whatever technological fix authorities propose. During the 6:30 p.m. presser, Sheriff Norris floated the need for “next-generation integrated command” and “inter-agency situational awareness.” By dawn, trade-journal e-blasts touted Palantir’s “Unified Fire Response” demo; an Idaho state-house committee scheduled emergency hearings on interoperability grants; and cable news panels echoed talking points about “silo-busting.” Webb stresses how quickly trauma becomes budget line-items: FEMA, DHS, DoD rural-counterterror funds. Psychological manipulation also extends to grief pacing: rumors of West-Webster-style suicides (a young man leaping from a Post Falls bridge after Roley’s death) link despair to the supposed lone shooter, cementing him as the sole villain and discouraging deeper inquiry. Meanwhile, community trust erodes; chiefs fear being next on a compromise tape; rank-and-file accept top-down integration as insurance against chaos. Thus, Webb argues, the psy-op doesn’t merely hide the operation—it actively recruits its future champions.
Part X – Conclusions and Forward Trajectory
Webb ends by acknowledging the personal stakes: “There’s no money in naming Mossad tactics on their home turf—only risk.” Yet he frames exposure as the lone antidote to creeping federalisation. In his narrative, Wes Roley is not the deranged shooter but the bait—possibly groomed since childhood—whose flamboyant persona lured Kootenai’s battalion chiefs into a prepared kill-zone. The real triggerman was a trained asset (Decker); the real mastermind, Greg Carr; the real objective, subjugating county-level autonomy under a national fusion-software regime that doubles as a land, mineral, and data grab. Parallels to Israeli art-student stings, Comverse wire-taps, and earlier fire-ambush cases reveal a template that can replicate in any rural county. Webb urges viewers to demand raw dispatch data, insist on third-party autopsies, and shield local software like Battalion 3 from federal “interoperability” mandates. Absent pushback, he warns, every house fire could become a pretext for armored incursions; every curious volunteer, a future patsy. Whether one buys every detail or not, the core claim is stark: sexual lures and surveillance patents remain evergreen tools for empire-builders, and small-town America is now the front line. “Cain still kills Abel,” Webb repeats, “but now he livestreams it in 4K—unless we pull the plug.”






















George do you ever sleep?
A frightening but all-too-real program to utterly destroy American independence and rural culture, and establish techno-fascist federal control by sociopaths and psychotics. It is clear America is under massive attack by forces inside and outside our own government. As Jeffrey Prather always says, "The first rule of war is to know you are in one." Thank you George for these reports.